Three Areas of Software Defects: Dev-Sec-Ops

Miles Lancaster
Architecture, Security, and Compliance
Modern business is deeply intertwined with technology. While this fosters an efficient environment, it also naturally brings risk. Our reliance on technology means now, more than ever, hardware and software bugs can wreak havoc on a company’s operations and reputation. Not to mention the cost of outages and prolonged application downtime!
But according to the IBM System Science Institute Relative Cost of Fixing Defects, it’s much more cost-effective to catch software defects in the early stages of development versus the later stages of the lifecycle.
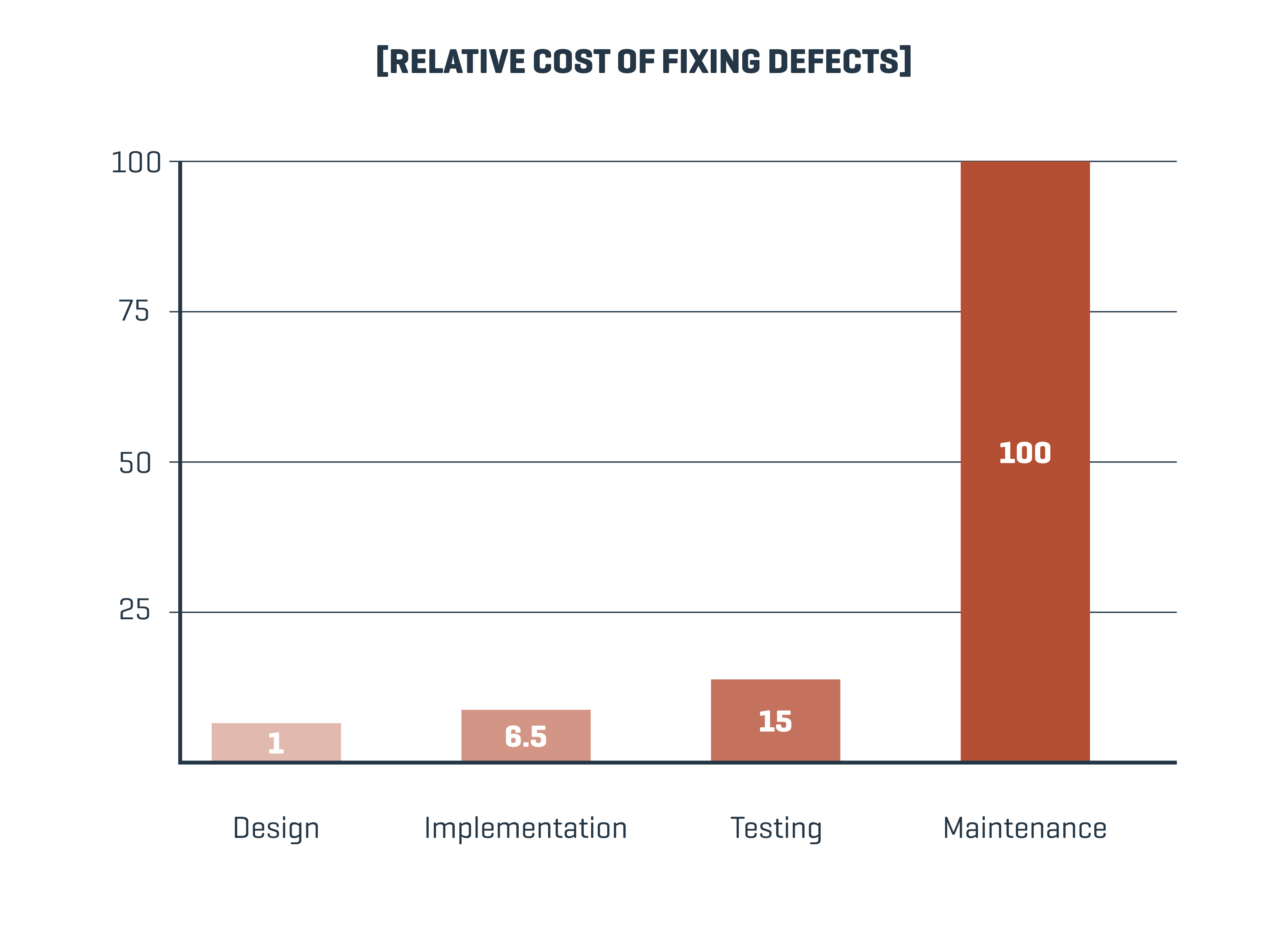
In other words, cleaning up defects after a vendor’s software is implemented into your systems can be a disaster for software performance and quality. But how can ITOps mitigate risk for software that’s not built in-house?
Traditionally siloed teams, like Security and Operations, are just that – siloed. And that siloed approach to managing defects in third-party software leads to IT risk. This isn’t new information. Everyone knows this, but there’s been little clarity on how to fix it in a repeatable, automated manner.
In this article, we’ll break down the impact of these defects and how to combat them in three key IT areas: Development, Security, and Operations – often referred to as Dev-Sec-Ops. We’ll explore how to mature your operations and transform your approach to defect management, driving your organization towards a more secure future.
3 Areas of Software Defects: Explained
For the past several years Development and Operations, or DevOps, have been working closer than ever so that internal software is successfully deployed. This collaboration results in efficiency and growth.
However, while DevOps fosters closer collaboration between Development and Operations teams – the same cannot be said for Security and Operations, a.k.a. SecOps.
1. Development: Where Software Defects Originate
Software defects are inevitable. They generally occur in the development phase of internal software. This phase involves a complex interplay of open-source components and custom-written code. The primary reason for defects is due to the multifaceted nature of the software development process.
Open-source components are ready-made solutions that companies often integrate into their projects. These can sometimes contain hidden defects, making them susceptible to various vulnerabilities or operational failures. When not meticulously integrated into a project, these open-source components can be the source of software defects that compromise the overall quality and security of the software.
Custom code, on the other hand, is specifically tailored to the needs of a project. However, it’s in this customization that software defects can happen. Developers might unknowingly introduce errors into the code, which can later show up as defects in the final product.
An integral part of the development phase is the quality assurance (QA) process. If the software fails to function correctly due to custom code issues, these defects should ideally be caught during the internal QA process. However, with the growing complexity of software, some defects may still slip through – underlining the need for rigorous testing in the development phase.
2. Security: Protecting Against Vulnerabilities
Security vulnerabilities are similar to unlocked doors in your system that malicious intent can find. These vulnerabilities open the door to potential breaches, data theft, and even financial losses.
To combat these vulnerabilities, Security teams employ mature processes and tools like the Common Vulnerabilities and Exposures (CVE) framework and the National Vulnerability Database. These resources help them identify, categorize, and mitigate vulnerabilities effectively.
Security vulnerabilities are very different from operational defects. That’s why distinguishing between operational defects and security vulnerabilities is vital. Operational defects most often appear as hiccups in an application’s performance. They might slow down a system, cause crashes, or affect the user experience. They can be massively disruptive, but generally don’t pose a direct security risk.
We argue that Ops teams need to be upgraded to reach a similar level of maturity in software defect management - on par with the maturity of security vulnerability management.
All technology vendors – including industry giants such as Cisco – have in-house developers who create software that may have operational or security defects. When companies purchase that third-party COTS (Common Off The Shelf) hardware and software, those defects fall to the Sec and Ops teams to manage.
This introduces compelling reasoning for treating defects under the guidance of both Operations and Security teams, SecOps. Shifting towards this perspective is an easy way for organizations to take a more holistic approach to defect management.
3. IT Operations: Overlooked Risk Factors
Unlike security vulnerabilities, third-party operational defects are often not fully considered. It’s crucial to focus now on IT Operations to ensure that all aspects of software defects are addressed. ITOps deals with the operations and maintenance of the software and hardware infrastructure that organizations rely upon.
Operational defects in vendor hardware and software can have an impact on the overall functionality of a company's systems, potentially causing disruptions. Security vulnerabilities get significant attention due to their potential for breaches and data loss, but operational defects can also lead to financial losses and downtime.
Addressing this often-neglected aspect is one way to create a multi-layered approach to software defect management. Companies can further fortify their systems availability and operational efficiency, making their entire IT estate more dependable.
How to Mature Your Organization & Become More Agile
Maturity in ITOps is essential for preventing and responding to software defects – especially for companies that need their applications to be available around the clock. Balancing the needs of different teams can be challenging, and security is often prioritized.
To help Ops get their time to shine, your organization may require a cultural shift with data to back it up – one that embraces open communication between traditionally siloed teams.
Every organization aspires to reach harmony with DevSecOps, but getting there can be quite challenging. Now there are modern solutions to automate your journey.
Try BugZero: Automated Defect Risk Management for ITOps
Enter BugZero, a solution for managing operational defects similar to how vulnerabilities are handled. We help organizations bridge the gap between Security and Operations.
By streamlining the operational defect management process and providing prioritization, BugZero is a practical first step for organizations.
Operational defects no longer have to be handled with disjointed, best-effort solutions. With BugZero, IT Operations can see all the critical vendor bugs specific to their technology products and versions, prioritizing the ones that need immediate attention. This helps foster collaboration between departments and pushes organizations toward the ultimate goal of DevSecOps maturity.
Learn why BugZero is the partner you need to help reduce risk, unite teams, and remain agile.
Do you know how much operational outages are costing you?
Understand the cost to your business and how BugZero can help you reduce those costs.
Latest news
Keep reading



