Accelerate your path to NIST Compliance
BugZero helps enterprise IT teams uncover and resolve non-security bugs that traditional CVE tools miss — ensuring full-spectrum risk coverage under NIST SP 800-53

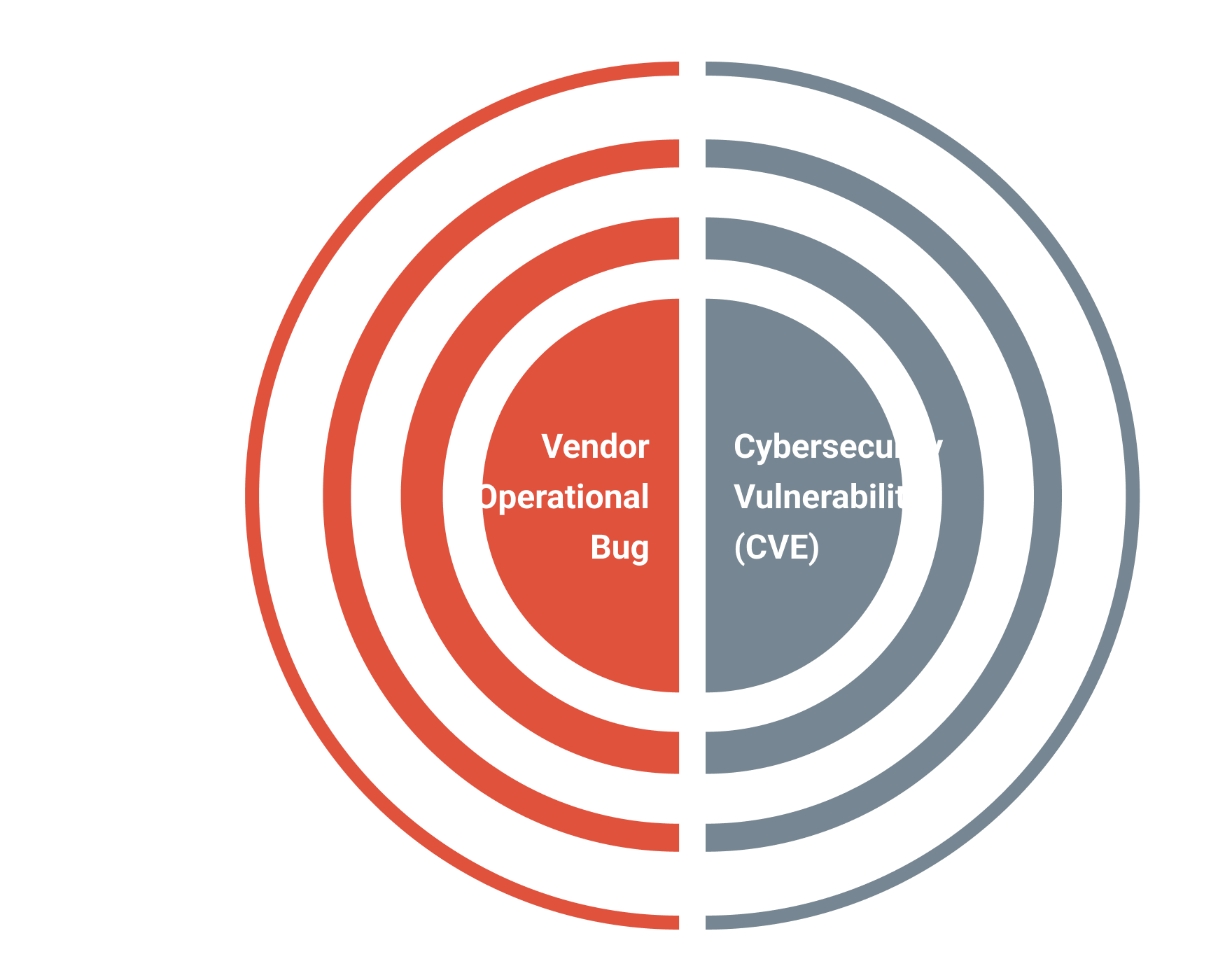
Organizations must identify and remediate all software and firmware flaws — including non-security bugs
The NIST Blind Spot
Security tools don’t catch everything — and NIST knows it
What does
NIST require?
NIST SP 800-53 requires organizations to identify all types of system flaws, not just security vulnerabilities.
Where do today's
solutions fall short?
Most tools focus only on CVEs while operational bugs from third-party vendors go untracked and unaddressed.
What is the impact
of non-compliance?
These overlooked issues can lead to outages, compliance gaps, and audit failures.
BugZero bridges the gap
BugZero consolidates and evaluates vendor reported operational bugs, not included in vulnerability management tools, to proactively address risks before they cause an outage

Consolidate reasonably identifiable vendor bug reports

Filter reports to find relevant risks to your environment

Enrich data with proprietary risk scoring and AI enhancements to inform prioritization

Prioritize risks in ServiceNow before an incident occurs
Comprehensive third-party risk
management across NIST controls
Specific NIST controls offer guidance and requirements around what needs to be done to effectively manage third-party IT risk
Flaw remediation
BugZero evaluates vendor reported non-security defects against your inventory and proprietary risk scoring to help your team prioritize remediation
Learn more >
Organizations must identify and remediate all software and firmware flaws — including non-security bugs

Automated integrity checks and timely alerts must be used to detect software errors and incidents from environment changes
Software & data integrity
BugZero continuously monitors and surfaces previously unaccounted for risks to protect system and data integrity
Learn more >Change configuration controls
BugZero surfaces risks in change tasks using contextual search and collects critical alerts from vendors related to misconfiguration risks to further reduce outages
Learn more >
All system modifications — planned or unplanned — must be reviewed, approved, tested, and audited through formal processes and automated tools
IT Service Manager
Fortune 500 Financial Services Firm