The missing piece in IT risk management
Proactively assess vendor reported operational bugs with BugZero to fill a critical gap in your IT risk strategy and maximize the availability and integrity of your environment
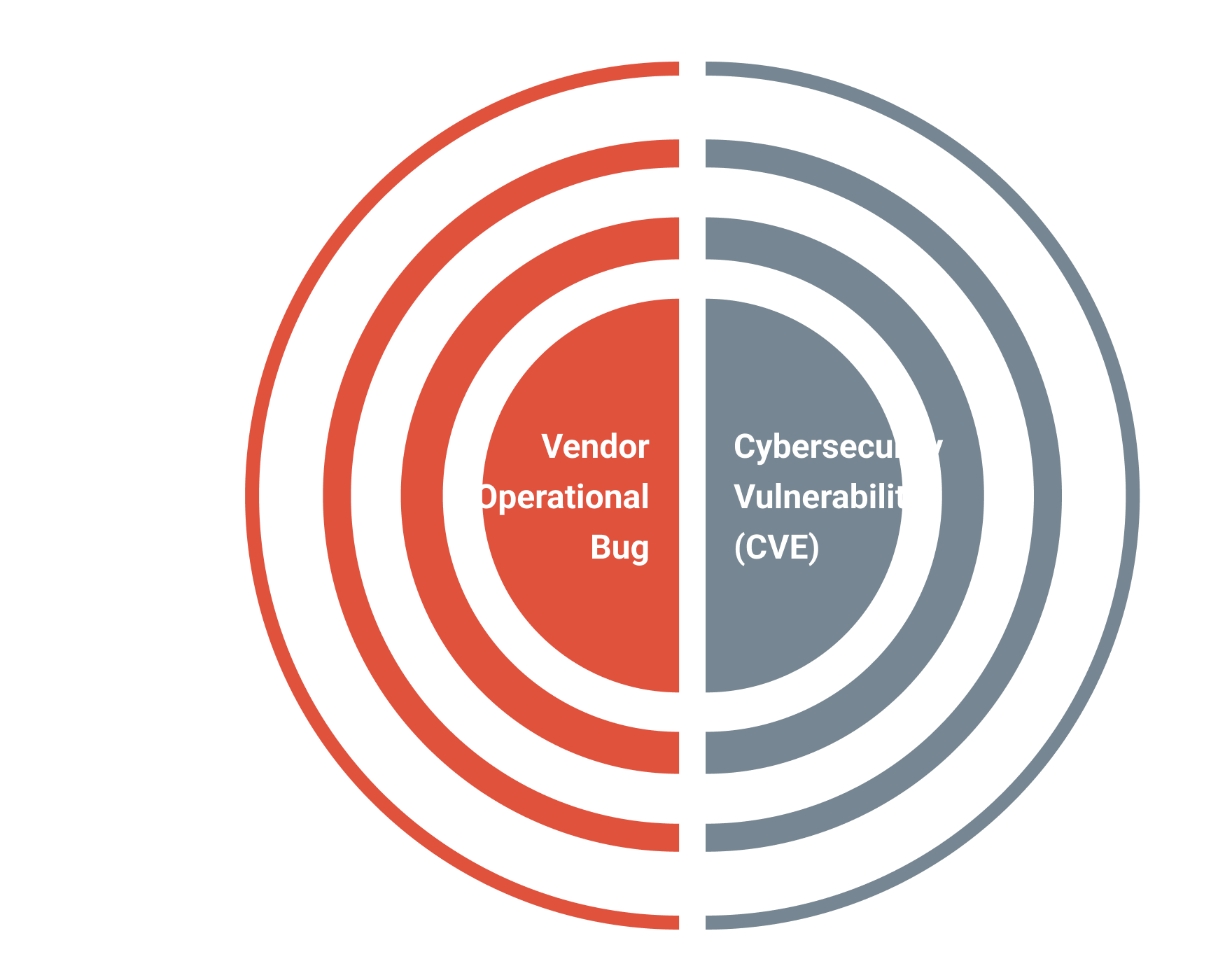
What is the difference?
Operational bug
A software flaw causing unexpected behavior that could impact the integrity or availability of your IT environment
Synonyms
Operational vulnerability, stability bug, non-security bug, defect, operational bulletin, known issue/defect
Cybersecurity vulnerability (CVE)
A vulnerability in your environment that could be exploited to the detriment of your business
Synonyms
Security vulnerability, exposure, threat, security advisory, security bulletin, and exploit
Operational bug vs. vulnerability management
Vendor reported operational bugs are NOT included in cybersecurity vulnerability management tools, and so are often ignored until after they cause an outage.
| Operational bug management tools | Vulnerability management tools | |
|---|---|---|
| Category | Vendor operational bug management | Vendor cybersecurity vulnerability management |
| Risk Focus | To protect from outages, system instability, operational data loss and performance degradation | To protect against cybersecurity breaches, data theft, and cybersecurity attacks that might compromise the organization |
| Solutions | BugZero | Rapid7, Tenable, Qualys, and others |
| Source | Operational defect database (Free resource created by BugZero through custom integrations with 100+ data sources) | National vulnerability database |
| Risk Quantification | Bug Risk Score (Learn more) | Common vulnerability scoring system (CVSS) |
| Change Risk Awareness | Flag risks on environment changes before they cause an incident | |
| Comprehensive Upgrade Risk Evaluation (Bug Scrubbing) | Operational bugs and CVEs | CVEs only |
| ITSM Integration | ||
| Real-time Monitoring | ||
| CMDB Mapping | ||
| AI Enrichment | ||
| Regulatory Compliance | DORA, NIST, FCA, and more | DORA, NIST, FCA, and more |
(Free resource created by BugZero through custom integrations with 100+ data sources)
(Bug Scrubbing)
Get proactive with operational bugs
Prioritize all vendor risks
Get proactive with operational bug risk mitigation, to compliment cybersecurity processes, and prevent outages
Bring certainty to change
Get ahead of the unknown by surfacing critical bugs in change requests before they cause an incident
Automate manual search
Consolidate operational bugs and CVEs in one place to automate bug scrubbing
IT Service Manager
Fortune 500 Financial Services Firm